Managing Keys and Certificates
Overview of key management options in Policy Manager for service, organization, container, and user identity categories.
Table of Contents
- Key Management Overview
- Key Management Functions
- Generate Options
- Import Options
- Export Options
- Delete PKI Keys and X.509 Certificate
- Assign PKI Keys and X.509 Certificate from User Keystore
Key Management Overview
Policy Manager provides key management that uses an "access key" encryption/decryption service to monitor access to Policy Manager functionality and managed web services. The "access key" guarantees message integrity by signing the message with a private key and verifying the message with a public key.
This enables you to publish the public key to an administrator or user, while retaining the private key. This means that any data that anyone else encrypts using your public key can only be decrypted by you.
The Policy Manager Manage PKI Keys Wizard is used to generate and manage (import/export) PKI Keys, Certificates, and Certificate Signing Requests for Service, Organization, Container, and User identities.
Supported Key / Certificate Types:
- PKI Keys—Access keys that guarantee message integrity by signing the message with a private key and verifying the message with a public key.
- X.509 Certificates—An authentication mechanism that provides visibility to public information and verifies private information while keeping it secure. Credential Information is embedded in the body of a SOAP message, or can be obtained from the HTTPS context.
- Certificate Signing Request (CSR)—A file that includes encoded information generated by a web server. It is sent from an applicant to the Certificate Authority to request a digital certificate. The CSR contains information identifying the applicant and the public key chosen by the applicant. Before creating a CSR, the applicant first generates a key pair keeping the private key secret. The corresponding private key is not included in the CSR, but is used to digitally sign the entire request.
Identity Categories
The Identity Categories section provides a functional overview of each identity category and available key management options for the default Policy Manager keystore or External Keystore feature.
External Keystore Feature
The External Keystore Feature enables a container to use an external key store for managing all the PKI keys and certificates it needs. If this feature is not installed, the default Policy Manager key store is used. The external keystore feature supports Physical HSM devices, Amazon AWS CloudHSM, and Entrust HSM device.
If an external keystore is configured, the private keys are stored in an external keystore. However, the X.509 CA certificate is stored in the Akana database keystore.
When using an external keystore, the "Generate X.509 CA Certificate and PKI Keys" and "Import X.509 CA Certificate and Private Key" options are not applicable. Instead, you must always use the assign "Key Alias" option.
If you need to use this feature, please contact Support.
Key Management Functions
The Manage PKI Keys Wizard supports the key management options listed below. Supported options vary based on the identity category and whether you are using the External Keystore feature. Refer to the Identity Categories topic for available key management options for the default Policy Manager keystore or External Keystore feature.
Note: Behaviors for each option are presented based using the "Default" Policy Manager keystore, and "External Keystore" (with External Keystore Feature installed).
Generate Options
Generate options are:
- Generate PKI Keys
- Generate X.509 Certificate
- Generate PKI Keys and X.509 Certificate
- Generate Certificate Signing Request (CSR)
Generate PKI Keys
The Generate PKI Keys screen uses the container to generate public and private keys. You must specify a key strength. The default key length is 1024 bits. The level of cryptographic strength of a key depends on its use (replacement schedule, security levels, and so forth).
- Default—Generates public and private PKI keys. This option does not create an X.509 certificate.
- External Keystore—This option is disabled for all identities if the External Keystore Feature is installed, because the PKI keys are stored in the external keystore.
Configuration:
- Select Generate PKI Keys. In the "Key Length" section, choose a key length based on your requirements. A longer key length is more secure but requires more processing.
- Click Finish. Certificate details are displayed on the Summary screen.
Generate X.509 Certificate
The Generate X.509 Certificate screen allows you to generate an X.509 certificate—an authentication mechanism that provides visibility to public information and verifies private information while keeping it secure. Credential information is embedded in the body of a SOAP message, or can be obtained from the HTTPS context.
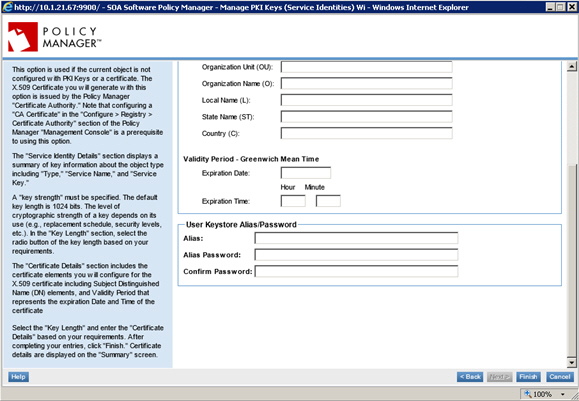
The "Certificate Details" section includes the certificate elements you will configure for the X.509 certificate, including Subject Distinguished Name (DN) elements and the Validity Period representing expiration date and time of the certificate.
- Default—Generates X.509 certificate and adds it to the existing PKI keys.
- External Keystore—Generates X.509 certificate and adds it to the external keystore alias that already includes PKI keys.
Configuration:
- Select Generate X.509 Certificate. Enter the "Certificate Details" based on your requirements. After completing your entries, click Finish. Certificate details are displayed on the Summary screen.
Generate PKI Keys and X.509 Certificate
The Generate PKI Keys and X.509 Certificate screen allows you to generate PKI Keys and an X.509 certificate. PKI Keys (access keys) guarantee message integrity by signing the message with a private key and verifying the message with a public key. An X.509 certificate is an authentication mechanism that provides visibility to public information and verifies private information while keeping it secure. Credential Information is embedded in the body of a SOAP message, or can be obtained from the HTTPS context.
You must specify a value for key strength. The default key length is 1024 bits. The level of cryptographic strength of a key depends on its use (replacement schedule, security levels, and so forth). In the "Key Length" section, select the radio button of the key length based on your requirements.
The "Certificate Details" section includes the certificate elements you will configure for the X.509 certificate, including Subject Distinguished Name (DN) elements and the Validity Period representing expiration date and time of the certificate.
- Default—Generates PKI keys and X.509 certificate.
- External Keystore—Assigns PKI keys and X.509 certificate to the external keystore alias of the current identity.
Configuration (Default):
- Select Generate PKI Keys and X.509 Certificate. Select the "Key Length" and enter the "Certificate Details" based on your requirements. After completing your entries, click Finish. Certificate details are displayed on the Summary screen.
Configuration (External Keystore)
- If you installed the External Keystore Feature, the Generate PKI Keys & X.509 Certificate screen will include a User Keystore Alias/Password option that allows you to define an alias (identity) to assign to the PKI keys and X.509 certificate being generated. These keys will be stored on your external keystore.
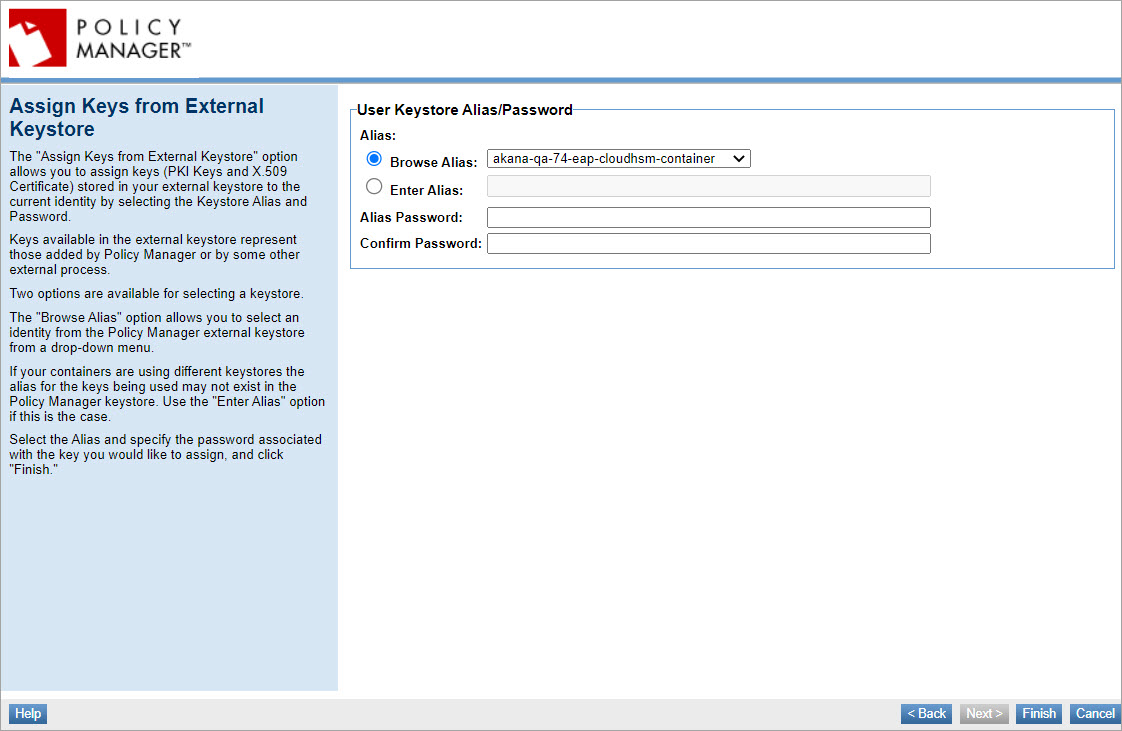
- You can then assign these keys to an identity category: on the Manage PKI Keys Wizard home page, select the Assignment Options > Assign PKI Keys and X.509 Certificate from User Keystore option. At the Assign Keys from External Keystore screen, two options are available for selecting a keystore:
Browse Alias—This option allows you to select an identity from the Policy Manager keystore from a drop-down menu.
Enter Alias—If your containers use different external keystores, the alias for the keys being used may not exist in the Policy Manager keystore. If this is the case, use the "Enter Alias" option to reference the alias name.
- After specifying an alias, you must specify the password to complete the configuration.
Generate Certificate Signing Request (CSR)
The Generate CA Certificate Signing Request screen is used to generate a Certificate Signing Request for the current container. The CSR can be sent to a third-party Certificate Authority to request an X.509 certificate.
A Certificate Signing Request (CSR) is a file that includes encoded information generated by a web server. It is sent from an applicant to a Certificate Authority to request a digital certificate. The CSR contains information identifying the applicant and the applicant's public key. Before creating a CSR, the applicant first generates a key pair, keeping the private key secret. The corresponding private key is not included in the CSR, but is used to digitally sign the entire request.
A CSR file typically has a .CSR extension but can have other extensions based on the source application that generated the file. The container supports the PEM (which is a BASE64-encoded PKCS10) for Certificate Signing Requests.
- Default—Used if the user of the container already has a PKI key pair and wants to generate a Certificate Signing Request. The request can be sent to a third-party Certificate Authority to request an X.509 certificate.
- External Keystore—No change.
Configuration:
- Select Generate Certificate Signing Request. Enter the "Certificate Signing Request Details" based on your requirements. After completing your entries, click Finish. Certificate details are displayed on the Summary screen.
Import Options
Import options are:
Import X.509 Certificate
The Import X.509 Certificate screen is used to import an X.509 certificate that has been issued by a third-party Certificate Authority (CA).
For importing a certificate, the import function supports .CER and .DER file formats.
- Default—Used to import an X.509 certificate that has been issued by a third-party Certificate Authority (CA). As a prerequisite to using this option, a PKI key pair must already by generated. The import function supports the certificate file format (.CER).
- External Keystore—Imports an X.509 certificate and adds it to the alias that already includes PKI key in the external keystore.
Configuration:
- Select Import X.509 Certificate. To specify the file location of the X.509 certificate, click Browse. The Choose File dialog displays. Navigate to the directory location where the certificate is stored, select the certificate file, and then click Open. The Certificate Path field is populated with the location of the X.509 certificate.
- Click Finish.
Import PKI Keys and X.509 Certificate
The Import Private Key and X.509 Certificate from Keystore screen is used to import keys and a certificate that has been issued by a third-party Certificate Authority.
For importing keys and certificate, the import function supports .JKS and .P12 file formats.
The "Keystore Details" section is used to configure the elements required to perform the import.
- Default—Used to import public and private keys and a certificate that has been issued by a third-party Certificate Authority. Import requires that you specify a keystore path or certificate filename. Supported keystore types include Java (imports public keys from a certificate only) and PKCS12 (imports keys from PKCS12 only). The import function supports the certificate file format (.CER).
- External Keystore—Imports PKI keys and X.509 certificate and assigns them to an external keystore along with the associated alias.
FIPS Support for importing external private keys: FIPS 140-2 level II allows import of external private keys. You cannot import external private keys into an HSM that is FIPS-140-2 level III compliant.
Configuration:
- Select Import Private Key and X.509 Certificate. Select the "Keystore Type" you would like to import (Java or PKCS12).
- To specify the file location of the X.509 certificate, click Browse. The Choose File dialog displays. Navigate to the directory location where the certificate is stored, select the certificate file, and then click Open. The "Keystore Path" is populated with the directory location of the X.509 certificate.
- Enter the "Keystore Password" for the certificate and confirm it.
- Click Load Aliases. The "Key Alias" drop-down list box is populated with a list of key alias entries that are defined in the specified keystore file. Select the key alias you would like to import from the drop-down list box. Enter the key password and confirm it.
- To import the private key and X.509 certificate, click Finish. The certificate is imported into the Policy Manager data repository.
Export Options
Export options are:
Export X.509 Certificate
- Default—Exports an X.509 certificate to certificate file format (.CER).
- External Keystore—No change.
Configuration:
- Select Export X.509 Certificate, choose a save option (Open with or Save File), and click OK.
Export Private Key and X.509 Certificate
- Default—Exports a private key and X.509 certificate to the certificate file format (.CER).
- External Keystore—This option is disabled for all identities if the External Keystore Feature is installed as the export of private (or secret) keys out of an HSM is restricted.
Configuration:
- Select Export Private Key and X.509 Certificate.
- Choose a save option (Open with or Save File), and then click OK.
Delete PKI Keys and X.509 Certificate
- Default—Deletes key of the current identity type from the Policy Manager default keystore.
- External Keystore—Deletes key of the current identity type from the external keystore. Note that you cannot delete a key if it assigned to one or more identities.
Configuration:
- Select Delete PKI Keys & X.509 Certificate.
- At the confirmation message, click OK.
Assign PKI Keys and X.509 Certificate from User Keystore
This option displays only if the External Keystore feature is installed.
- Allows you to assign keys that are already added to the HSM or JCEKS External Keystore to the current identity.
- Keys available in the HSM or JCEKS External Keystore represent those added by Policy Manager or by some other external process.
- To assign keys, select the alias name and password associated with the key you would like to assign. (pmdomain)
The "Assign PKI Keys and X.509 Certificate from User Keystore" option allows you to assign keys to various identity categories, including Service, Organization, Container, and User, as well as the Certificate Authority (CA) and Policy Manager Domain (pmdomain).
Related Topics