Identity Categories
Overview of Service, Organization, Container, and User identity categories and associated key management functions.
On this page:
Overview
Key management can be performed on Service, Organization, Container, and User identity categories using the Manage PKI Keys Wizard. As a prerequisite to performing key management tasks using the Manage PKI Keys Wizard you must define a CA Certificate in the Configure > Security > Certificates > Certificate Authority section.
This topic includes:
- Functional description of each identity category.
- Description of what type of key management is supported for the identity category by the Manage PKI Keys Wizard.
- Location of the Manage PKI Keys function in the Policy Manager Management Console.
- Screen capture of the initial page that shows what functions are available for the identity category for the default Policy Manager Keystore and External Keystore Feature.
Key management options that are grayed out are not available for the identity type. See Managing Keys and Certificates for a list of available options. To perform a key management task, select the desired option, and follow the wizard help text and prompts.
Note: The Generate PKI Keys and Export Private Keys and X.509 Certificate options are grayed out (i.e., not available) for all Manage PKI Keys Wizard when the External Keystore Feature is installed.
Service Identities
- Represents the default service identity in the local domain.
- Every service has one identity by default.
- A service can be assigned a single key identity and can be deployed in multiple containers. The complete service identity is then represented by the service key plus the container listener configuration, and defined service path.
- Policy Manager uses the service identity to associate the PKI keys to the service.
- The username for service identity is derived from a service key.
- User identities are not displayed anywhere in the configuration screens with the exception of on the Service Details page to indicate the default username of the service.
- PKI Keys of the service are managed from the Service Details page using the Manage PKI Keys option by anyone that has the Service/Modify permission.
Configuration
The Manage PKI Keys (Service Identities) Wizard provides key management options that allow you to generate public and private keys to facilitate service access. A service can be assigned a single key identity and can be deployed in multiple containers.
Location:
Service Details > Manage PKI Keys (from Actions portlet)
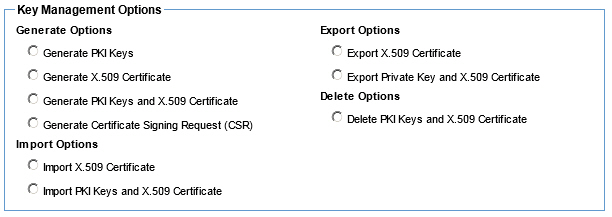
Manage PKI Keys (Service Identities) - Available options using the default Policy Manager keystore
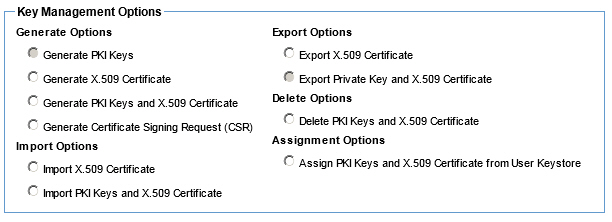
Manage PKI Keys (Organization Identities) - Available options using the External Keystore feature
Organization Identities
- Also referred to as a consumer identity.
- This identity is assigned to the organization.
- Organization administrators can fully manage these identities (i.e., create, update, view, delete, associate PKI keys).
- A consumer identity is used to model any application that is consuming web services, but it itself is not a web service. If the consumer is a web service, user can model the service using the service artifact.
- To model all consumers that are not services, Policy Manager uses Organization Identities (or consumer applications or application users). Therefore, these and web services represent consumer applications, these are visible along with services in the Contract's Consumer identities portlet for selecting the consumers of the contract.
- These identities are assigned only to contracts.
- One consumer application identity belongs to one organization only like the service belongs to one organization.
- Consumer applications can be local domain users or external domain users (like LDAP users).
- PKI Keys of the organization identity are managed from the Organization Details page using the Manage PKI Keys option by anyone that has the Organization/Modify permission.
Configuration
The Manage PKI Keys (Organization Identities) Wizard provides key management options that allow you to generate public and private keys to facilitate consumer applications that will be accessing an Organization. Consumers (other than Services) are identified in Policy Manager with an identity. Identity can be an external domain user or local domain user.
Location:
Organization Details > Organization Identities Portlet > Manage PKI Keys (from drop-down menu)
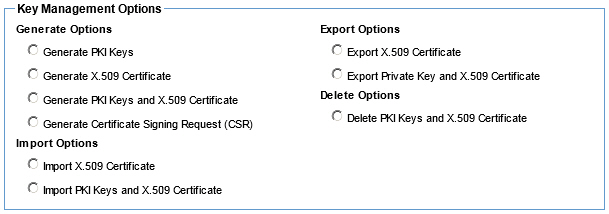
Manage PKI Keys (Organization Identities) - Available options using the default Policy Manager keystore
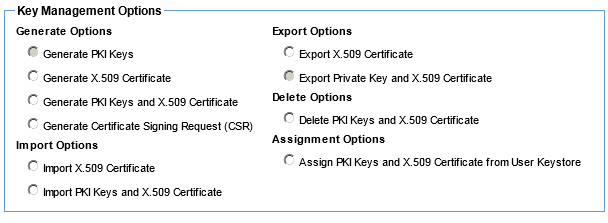
Manage PKI Keys (Organization Identities) - Available options using the External Keystore feature
Container Identities
- A container identity stores the identity of the container and the inbound/outbound HTTPS certificate with private key.
- Every container has one identity by default.
- Policy Manager uses the container identity to associate the container seed and PKI keys to the Container.
- It is also used to associate the inbound SSL and outbound SSL certificate and private key to Containers.
- This identity is not displayed anywhere
- The container identity is a local domain.
- PKI Keys of the container identity are managed from the Container Details page using the Manage PKI Keys option by anyone that has the Container/Modify permission.
Configuration (Containers - Inbound)
The Manage PKI Keys (Containers - Inbound) Wizard provides key management options for inbound certificates that are used if you want a container to receive HTTPS messages with client authentication to the next hop.
Location:
Container Details > Inbound Listener Portlet > Manage PKI Keys (from Actions drop-down menu)
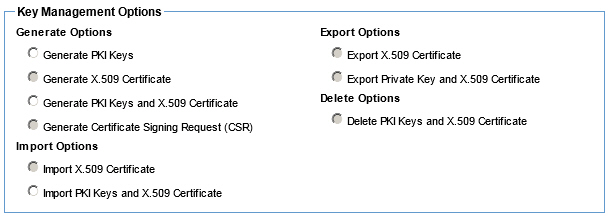
Manage PKI Keys (Containers -Inbound Identities) - Available options using the default Policy Manager keystore
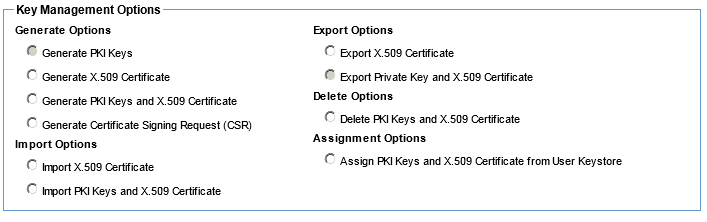
Manage PKI Keys (Containers - Inbound Identities) - Available options using the External Keystore feature
Configuration (Containers - Outbound)
The Manage PKI Keys (Containers - Outbound) Wizard provides key management options for Outbound certificates that are used if you want a container to receive HTTPS messages with client authentication to the next hop.
Key Configuration Prerequisites
As a prerequisite for configuring outbound HTTPS certificates, you must have previously imported Trusted CA Certificates using one of the following options:
- In the Configure > Security > Trusted CA Certificates section of the Management Console, you imported Trusted CA Certificates (.CER only) using the Add Trusted CA Certificate option.
- On the Configure > Security > Trusted CA Certificates section of the Management Console, you imported Trusted CA Certificates from a keystore using the Import Trusted CA Certificate from Keystore option.
Trusted CA Certificates imported using any of the these options will display on the "Trusted CA Certificates Summary" screen in the Configure > Security > Trusted CA Certificates section of the Management Console.
Outbound HTTPS Usage Scenarios
Outbound HTTPS containers are used in the following scenarios. Note that Outbound HTTPS is only necessary if you want HTTPS between Network Director and Policy Manager:
- Policy Manager uses outbound HTTPS certificate if it has to access WSDLs using URLs that require client authentication.
- Policy Manager uses outbound HTTPS certificate if it is discovering services from the Container Agents that require client authentication.
- The Policy Manager Container and Container Cluster (for Policy Manager 8.x), and Container, Container Cluster, 5.2 Standalone Management Point, and 5.2 Embedded Management Point Containers (for Policy Manager 7.x) could use outbound HTTPS certificate.
- 5.2 Standalone Management Point Containers (PM7x) could use an outbound HTTPS certificate if it has to send the request to next hop over HTTPS protocol that requires client authentication. In this scenario, policy configuration provides an option to not use the container outbound HTTPS certificate for HTTPS connection with next hop and instead use Service certificate/private key.
Location:
Container Details > Outbound Configuration Portlet > Manage PKI Keys (button)
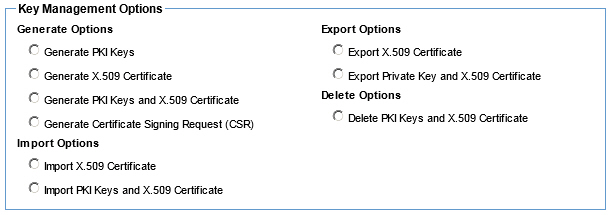
Manage PKI Keys (Containers -Outbound Identities) - Available options using the default Policy Manager keystore
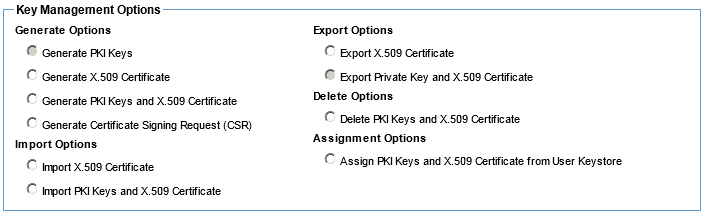
Manage PKI Keys (Containers - Outbound Identities) - Available options using the External Keystore feature
User Identities
- End users are users of the consumer application. For example, if a portal application is a consumer application, users of the portal application becomes end users of Policy Manager.
- End user authorization is done in the Container using Authorization Policy.
- End users authorization rules are defined in the Service Authorization Rules tab of the Organization.
- End users do not belong to organizations.
- The same end user can access the services of different organizations and may not even belong to any of the organizations in Policy Manager.
- These users most often come from other user repositories like LDAP.
- If you want to use local domain users, these users must be created in the Security > Users tab using the Add User function, which means it is a System administrator function.
- Though users are created by System Administrators, every Organization Administrator has to allow the user to access the services of their organization by creating the service authorization rules.
- End Users can be Local Domain users or external domain users (like LDAP).
- PKI Keys of the service are managed from the Security > Users page using the Manage PKI Keys option the System Administrator and Organization Administrators with Full Control permission.
Configuration (Users)
The Manage PKI Keys (Users) Wizard provides key management options that allow you to generate public and private keys to facilitate user authentication process.
Location:
Security > Users > Manage PKI Keys (button)
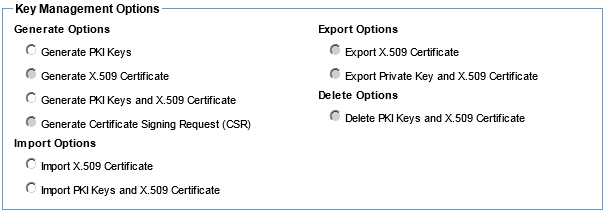
Manage PKI Keys (User Identities) - Available options using the default Policy Manager keystore
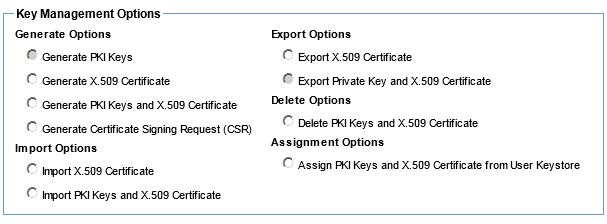
Manage PKI Keys (User Identities) - Available options using the External Keystore feature
Related Topics