Using SAML for Single Sign-On in the Akana Platform
Instructions for configuring a SAML Web SSO domain and enabling single sign-on login for Community Manager.
Table of Contents
- Prerequisites
- Configuration on Policy Manager
- Configuration on Community Manager
- Steps to Verify the SSO configuration
Prerequisites
Before you start, do the following:
- Install the Akana SAML 2.0 Web Browser SSO Service Provider plug-in on the Community Manager container.
- Install the Akana SAML 2.0 Web Browser SSO Service Provider UI plug-in on the Policy Manager container.

- Generate the metadata.xml file from your SAML identity provider and have it ready.
Configuration on Policy Manager
- Log in to Policy Manager.
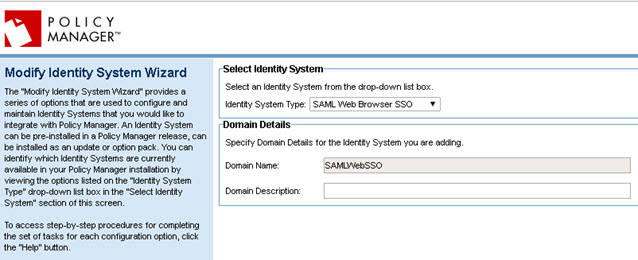
- Navigate to Configure > Security > Identity Systems > Add Identity System.
- From the Identity System Type drop-down list, select SAML Web Browser SSO.
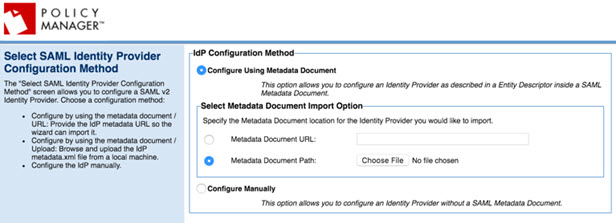
- Upload the metadata.xml file from your SAML identity provider, and then click Next.
- If the Entity ID is not automatically populated, provide it. Then, select the appropriate Authentication URLs and Logout URLs, as shown in the example below.
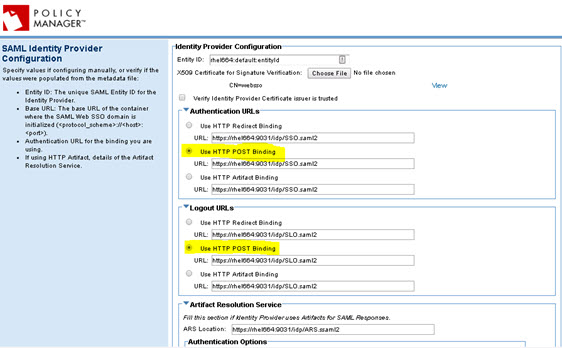
- Make sure the options below are selected, and with the correct values, and that the Entity ID and Base URL values match the values from your SAML identity provider.
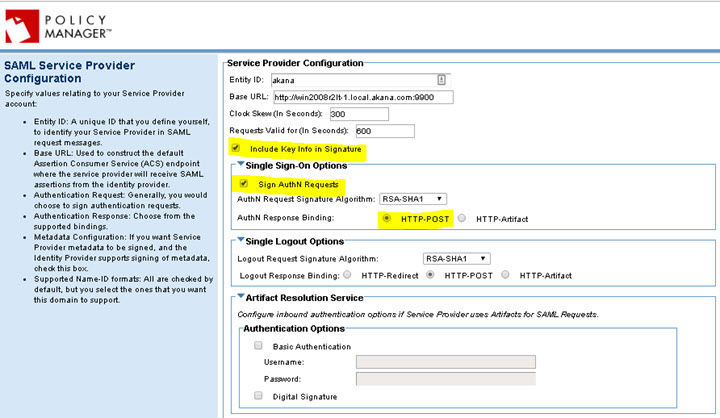

- Create a self-sign certificate, and upload the certificate to your SAML identity provider (or use the Import PKI Keys & X509 Certificate feature and upload the certificate to your SAML identity provider).
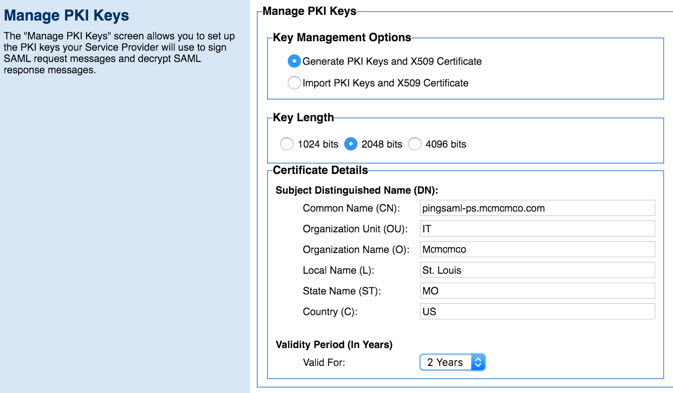
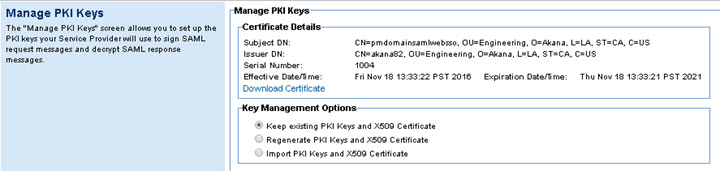
Note: Download the cert to your local folder, and then upload it to your SAML identity provider. The provider can use this certificate to encrypt the SAML Assertion.
- Attribute Mapping must match with your SAML identity provider's configuration.
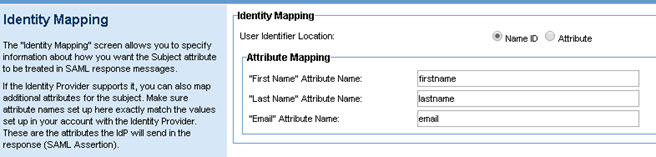
Configuration on Community Manager
- Log in to the Community Manager developer portal.
- Go to More > Admin > Logins.
- Select the check box next to the SAMLWebSSO domain to enable it as a platform login domain, and then click Save.
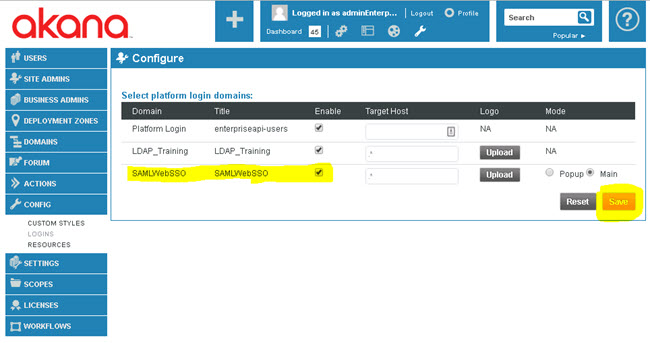
- Optional, required only if the same LDAP is used and users are already logged in to CM with LDAP domain: In the database, move all the users from the LDAP domain to the SAML Web SSO domain.
Steps to Verify the SSO configuration
- In the Community Manager developer portal, in the Login page, select the SAML login domain, as shown below.
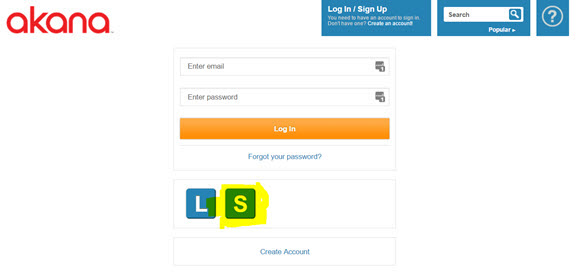
- Verify that the user is taken to the SAML SSO login page for your provider, as shown in the example below. Enter the LDAP credentials, and then click the Sign On button.
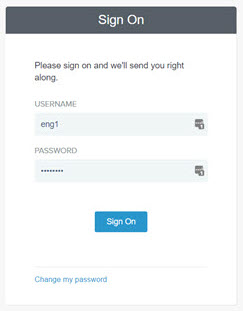
- Verify that the user is successful in logging in to Community Manager using the LDAP credentials configured for SAML.