Enabling IAM Token-Based Authentication for Amazon RDS
You can connect to an Amazon Relational Database Service (Amazon RDS) database (DB) instance by using AWS Identity and Access Management (IAM) authentication tokens instead of the native authentication methods. With the IAM authentication token, you can securely connect to a database instance without a password.
The AWS IAM feature is certified for use with MySQL and Aurora MySQL-compatible databases.
Table of Contents
- Overview of AWS IAM
- Prerequisites
- Configuring IAM on Policy Manager and Community Manager Containers
- Optional: Enable SSL
Overview of AWS IAM
With the AWS Identity and Access Management (IAM) service, you can manage access to various AWS resources, including Amazon RDS (Relational Database Service) instances. IAM authentication is designed to provide enhanced security for RDS instances by supporting authentication with AWS IAM credentials instead of traditional database credentials.
IAM authentication offers the following advantages over traditional database authentication:
- Enhanced security: You can manage user access by using AWS IAM policies, which provide precise control and are simpler to manage than database-level users and passwords.
- No database credentials: Using IAM authentication, you avoid the requirement to store and manage database credentials, thus reducing the risk of unauthorized access and potential credential leakage.
- Integration with AWS services: IAM authentication integrates with AWS services like Amazon Redshift, S3, and AWS Glue, supporting consistent authentication through IAM roles.
- Multifactor authentication (MFA) support: IAM authentication supports MFA, adding an additional layer of security for RDS instances.
Prerequisites
You can connect to an RDS for MySQL or Aurora MySQL DB instance. If you are using Aurora MySQL 8, complete the following steps to fulfill the prerequisites:
To set up IAM DB authentication with Aurora MySQL 8
- Create an Amazon RDS instance and specify the Aurora MySQL 8 type with Serverless v2 capacity settings. For more information, see Creating an Amazon Aurora DB cluster.
- Enable IAM database authentication on DB instances or DB clusters. For more information, see Enabling IAM database authentication.
- Create an IAM role and attach an inline policy to map the database user to the IAM role.
For more information, see IAM roles for Amazon EC2. Use the following structure to allow a user to connect to a DB cluster.
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "rds-db:connect" ], "Effect": "Allow", "Resource": "arn:aws:rds-db:{region}:{Account ID}:dbuser:{db_user}" } ] } - To allow database authentication, attach the IAM role to the Amazon Elastic Compute Cloud (EC2) or Amazon Elastic Kubernetes Service (Amazon EKS) instance. Refer the instructions for attaching an IAM role to an instance as described in IAM roles for Amazon EC2.
- To identify the IAM role and connect to the Amazon Elastic Compute Cloud (EC2) or Amazon Elastic Kubernetes Service (Amazon EKS) instance, generate an AWS authentication token by running an AWS CLI command with the following structure:
aws rds generate-db-auth-token --hostname {db-instance-endpoint} --port {db_port} -- region {aws_region} --username {db_username} - Connect to the MySQL DB instance with the generated IAM authentication token by running a command with the following structure:
mysql --host=$RDSHOST --port=3306 --ssl-mode=VERIFY_CA --ssl-ca=/var/mysql-certs/rds-combined-ca-bundle.pem --user={db_user} --password={IAM_TOKEN} --enable-cleartext-plugin - Optional: Enable SSL.
Configuring IAM on Policy Manager and Community Manager Containers
To complete the process of enabling IAM database authentication, you must configure IAM on your Policy Manager and Community Manager containers. To help simplify this process, you can use an automation recipe. Follow the instructions in Configuring IAM on Policy Manager and Community Manager Containers.
Optional: Enable SSL
To enable SSL on a database for secure communication between the Amazon RDS instance and EC2 instance, change the require_secure_transport parameter value to 1. By default, the require_secure_transport parameter is set to OFF. To enhance the security of your DB instance, update the DB Parameter groups to use SSL and set the require_secure_transport parameter to ON. In this way, you can help to ensure that connections to your DB instance are encrypted and secure.
The following instructions are necessary only when SSL is enabled for communication between the Amazon RDS database and Akana.
To enable communication between the Amazon RDS database and Akana over SSL
- Download the certificate bundle file or SSL certificate file. For more information, see Download the SSL certificate file.
- Set up the Java Database Connectivity URL by taking one of the following actions:
- Log in to the Admin console.
Go to the Configuration tab > Configuration Categories > com.soa.database.config and update the URL property to point to the keystore file.
- To specify the location, use the following structure:
jdbc:mysql://{server}:{port}/{database}?connectTimeout=60000&socketTimeout=60000&zeroDateTimeBehavior=convertToNull&useTimezone=true&useLegacyDatetimeCode=false&serverTimezone=GMT&characterEncoding=UTF-8&sslMode=VERIFY_CA&trustCertificateKeyStoreUrl=file:/<path to keystore>/AWS_RDS_CA.jks&trustCertificateKeyStorePassword=passwordSet up the JDBC URL by adding a URL property before installing the containers. Use the following structure for the property:
echo "url= jdbc:mysql://{server}:{port}/{database}?connectTimeout=60000&socketTimeout=60000&zeroDateTimeBehavior=convertToNull&useTimezone=true&useLegacyDatetimeCode=false&serverTimezone=GMT&characterEncoding=UTF-8&sslMode=VERIFY_CA&trustCertificateKeyStoreUrl=file:/<path to keystore>/AWS_RDS_CA.jks&trustCertificateKeyStorePassword=password" >> recipe.properties- To enable the changes, restart the container.
- To set up the URL with SSL, complete the following steps:
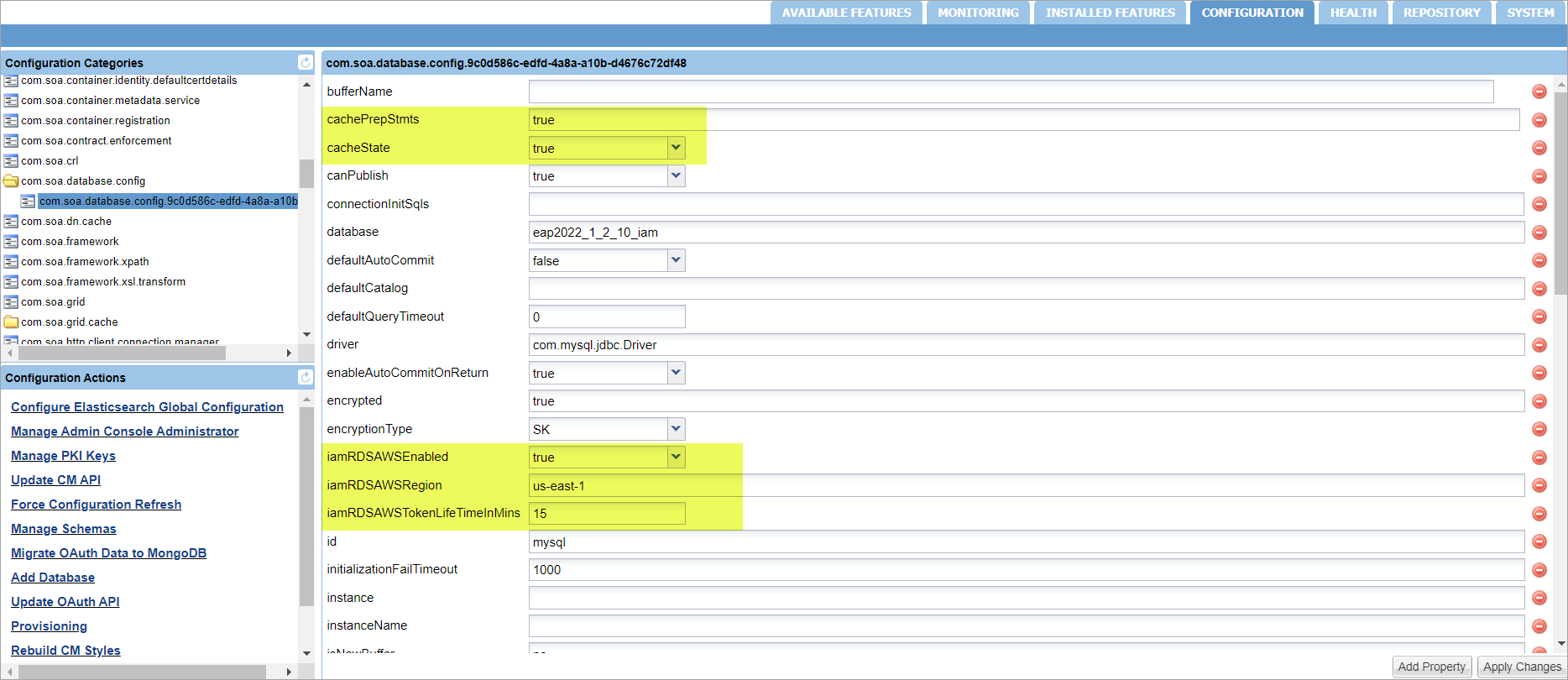
The properties cachePrepStmts, cacheState, IAMRDSAWSENABLED, IAMRDSAWSREGION, and IAMRDSAWSTOKENLIFETIMEINMINS are visible on Administration console under the com.soa.database.config PID.
Download and import the certificate bundle file or SSL certificate file
To enable SSL, you must download a certificate .pem file, create a keystore file, and then import the .pem file into the keystore file.
- To download the Amazon RDS Certificate pem file, run the following command:
sudo wget https://s3.amazonaws.com/rds-downloads/rds-combined-ca-bundle.pem
- Create an AWS_RDS_CA.jks keystore file and import the Amazon RDS Certificate .pem file into the keystore file by running the following command:
keytool -import -alias rds-root -keystore clientkeystore -file rds-combined-ca-bundle.pem
Confirm that the keystore is updated successfully.