Updating Certificates
Learn about the steps you should take when a certificate expires or is compromised.
On this page:
Overview
The Akana platform uses certificates in several different scenarios.
Certificates might be:
- Self-signed (generated by the platform)
- Generated by an external certificates authority (CA)
there are two main reasons why you might need to replace a certificate:
- The certificate is about to expire or has expired. This is the usual scenario.
Note: We strongly recommend that you do not let a certificate expire. Replace the certificate before it expires.
- The certificate has been compromised. This is rare.
This document covers the high-level steps you'll need to take when a certificate expires or is compromised.
Types of Certificates
The Akana platform uses certificates for the following:
- Container (Network Director, Policy Manager, Community Manager, or other containers): see Updating the Container Certificate.
- Listener certificate (for a secure listener): see Updating the Listener Certificate.
- Policy Manager domain certificate: see Updating the Policy Manager Domain Certificate.
Updating the Container Certificate
You can update the container certificate in the Akana Administration Console for the applicable container: Akana Administration Console > Configuration > Configuration Actions > Manage PKI Keys.
If the certificate for a container is expired, or close to expiration, the best way to update it is to get a new certificate. It's not necessary to update the private key just because the certificate has expired. Instead, you can generate and upload a new certificate using the same public/private keypair.
There are just a few steps in this process. The procedures below summarized these steps, with links for more detailed instructions.
Below are instructions for two common scenarios:
- Self-signed certificate: To update an expired certificate for a container by generating a new X.509 certificate
- External certificate authority: To update an expired certificate for a container by generating a new CSR request
To update an expired certificate for a container by generating a new X.509 certificate
If your container uses a self-signed certificate, you can just generate a new certificate. Follow the instructions:
- Open the Akana Administration Console for the container: Configuration > Configuration Actions > Manage PKI Keys. Under Key Management Options, choose Generate X.509 Certificate. Click Next.
- In the Generate X.509 Certificate page, enter the details for the certificate: Common Name (CN), Organizational Unit (OU), and so forth. Specify expiration date and time and then click Finish.
- At the Summary page, click Close.
- Now, update the certificate for the container:
- In Policy Manager Workbench, navigate to the container.
- On the right, under Actions, click Manage Container Certificate.
- On the Import X.509 Certificate page, in the New Certificate section, browse to the location of the new certificate and upload it.
- Restart the container.
- Test to make sure that your container is working correctly.
To update an expired certificate for a container by generating a new CSR request
When you generate a new Certificate Signing Request (CSR) for the container, the platform generates a certificate.csr file. You can then send the file to your Certificate Authority to get a new certificate.
- Open the Akana Administration Console for the container: Configuration > Configuration Actions > Manage PKI Keys. Under Key Management Options, choose Generate Certificate Signing Request (CSR), as shown below. See Generate Certificate Signing Request (CSR). Note that you don't need to update the private key unless it's been compromised. A new certificate can reference the same key pair.
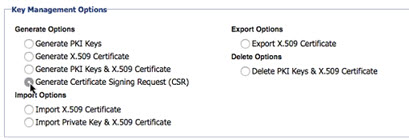
When you complete the wizard, the certificate.csr file is saved to your default folder for downloads.
- Send the certificate.csr file to your Certificate Authority, or your security team. Once the signing process is complete, you'll receive a new certificate.
For an example of all the steps of the certificate process, see Step 6: Create the keystore/certificate (UK Open Banking use case).
- Upload the new certificate for the container.
In the Akana Administration Console for the container: Configuration > Configuration Actions > Manage PKI Keys. Under Key Management Options, choose Import X.509 Certificate, as shown below. Browse for the certificate, and import it.
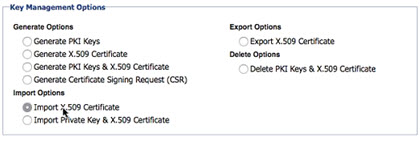
- Refresh the metadata for your container. Metadata refresh is necessary for the new certificate to take effect.
In Policy Manager, on the right, choose Workbench. On the left, select the container. On the right, under Actions, choose Update Container Metadata. For more information, see Update Container Metadata.
- Restart the container.
- Test to make sure that your container is working correctly.
Updating the Listener Certificate
To update the certificate for a listener, go to the listener:
Policy Manager > container cluster > container > Listener > Manage PKI Keys.
The key management options are similar to those shown above.
Updating the Policy Manager Domain Certificate
To update the Policy Manager domain certificate, go to:
Policy Manager > Configure > Security > Details > Manage PKI Keys.
The key management options are similar to those shown above.
Valid in version: 2020.1.2: When the Policy Manager domain certificate is updated, you do not have to restart Network Director containers to update the certificate information.
Versions prior to 2020.1.2: when done, restart Network Director containers so that the certificate information is refreshed.
Note: When you've updated the Policy Manager domain certificate, check if one or more of the Policy Manager service certificates might need to be updated also. By default, the Policy Manager services use the certificate of the first Policy Manager container that's created, so if the Policy Manager domain certificate expires, one or more of the service certificates might also have expired. If needed, to update the certificate for many services, contact Customer Support.
Compromised Certificate
If a certificate is compromised—for example, if a private key is shared—you will need to take additional steps to help ensure the security of your API Platform.
In this scenario, contact Customer Support for recommendations and assistance.