External OAuth Provider Domain
Configure an External OAuth Provider domain on the platform.
Note: For general information about platform domains, or specific information on a different domain, refer to Domains.
On this page:
- When would I choose an External OAuth Provider domain?
- What do I need to do to use the External OAuth Provider domain for PingFederate access?
- How do I add an External OAuth Provider domain?
- How do I add an External OAuth Provider domain with a FAPI security profile?
- What are the settings on the External OAuth Provider Configure page and what options should I choose?
- What are the settings on the Provider page and what options should I choose?
- What are the settings on the External OAuth Provider Access Token Validation page and what options should I choose?
- What are the settings on the External OAuth Provider Access Token Validation page for PingFederate?
- What are the settings on the External OAuth Provider Extensions page for PingFederate, and what options should I choose?
- How do I modify an External OAuth Provider domain?
- How do I delete an External OAuth Provider domain?
- How do I monitor the PingFederate Client Registration Status?
- How do I configure encryption key rotation for an External OAuth Provider domain?
When would I choose an External OAuth Provider domain?
If your installation uses any external OAuth provider, such as PingFederate or even the Akana OAuth Provider in a different installation, you can choose the External OAuth Provider domain option. Using this option, you can implement multiple OAuth Providers in the platform.
For example, you might have two installations; one has the platform OAuth Provider, and the second does not, but wants to integrate with the platform OAuth Provider. You could use this domain to accomplish that, configuring this domain to reference the external Akana OAuth Provider.
If you are using PingFederate, and were previously using the PingFederate domain option, we recommend that you switch to the External OAuth Provider domain. This domain is more flexible and also offers auto-configure of apps that have active contracts with APIs that reference the External OAuth Provider domain. Manual configuration of the apps in PingFederate is not necessary.
Note: If you are setting up the platform for the first time and want to use the External OAuth Provider domain to support PingFederate, note that the platform Administrator will also need to install the PingFederate options pack. If the PingFederate domain is not available on the domains list, it was not installed.
You can also use this domain type for any other entity that could be an external OAuth provider for your installation; for example, if your APIs offer services to app developers who use Google services, you might want to set up Google as an external OAuth provider. In the External OAuth Provider Domain, under Provider Type, choose Other, and then provide the necessary values provided at the Well-Known Configuration URL (for Google, it is https://accounts.google.com/.well-known/openid-configuration).
Note: If you want to use an External OAuth Provider domain for user login only, and the provider uses OpenID Connect for authentication, you don't need to configure an External OAuth Provider domain. Instead, choose the OpenID Connect Relying Party domain.
What do I need to do to use the External OAuth Provider domain for PingFederate access?
It's best to use the External OAuth Provider domain for your PingFederate implementation, because this domain supports integrated workflow for client registration out of the box. All you need to do is set up the domain: See How do I add an External OAuth Provider domain? below. Certain fields are available only for PingFederate users, as noted.
How do I add an External OAuth Provider domain?
The Business Admin can set up an External OAuth Provider domain in the Community Manager developer portal user interface.
Note: Adding or modifying the domain configuration settings on the platform does not add or modify configuration with the OAuth Provider itself. If you make changes to the configuration settings that are read from the Well-Known Configuration URL, it does change the configuration of the external OAuth provider. You must set up values in the platform to match the configuration of the OAuth Provider.
To configure an external OAuth Provider domain
- Log in as a Business Admin and go to the Admin section.
- Click Domains.
- Click Add Domain and choose External OAuth Provider. The Add External OAuth Provider Domain wizard opens at the Details page. This wizard has five pages:
- Enter a name and description for your external OAuth provider (for example, Name=PingFederate, Description=PingFederate Domain).
- Click Next to go to the Configure page, where you can specify the type of external provider and how you want to configure the provider. Specify values or choose options.
For more information, see What are the settings on the External OAuth Provider Configure page and what options should I choose?
- Click Next to go to the Provider page. This page includes information about the external OAuth Provider. If you provided a Well-Known Configuration URL to configure your domain, the information is read from the configuration file, but you can remove values if needed. Do not add values; if the provider doesn't support them, they won't work. If you are doing manual configuration you must specify the values.
For more information, see What are the settings on the Provider page and what options should I choose?
Note: Whether you upload information from a configuration URL, or enter it manually, be aware that the only effective values you can choose are values supported by the OAuth Provider. If you choose values that your OAuth Provider doesn't support, they will not work, and your choices could result in errors for the users of your API.
- Click Next to go to the Access Token Validation page. If you want the access token to be validated by the Resource Server, click the check box and specify values that will be needed for the validation, such as claim names and keys. For more information see What are the settings on the External OAuth Provider Access Token Validation page and what options should I choose?.
Note: On the Access Token Validation page, additional fields are available for PingFederate users only.
- Click Next to go to the Extensions page. If your external OAuth Provider supports one or more extensions, you'll see them in this tab. Check the box if you want your External OAuth Provider domain to support a specific extension that your external OAuth Provider offers, and then enter values associated with the extension. If you need help with any of the fields, check with your external OAuth Provider.
For an example of the properties you might see if you're using PingFederate, see What are the settings on the External OAuth Provider Access Token Validation page for PingFederate?
- Click Save. The External OAuth Provider domain is saved, and is now available for selection by API Admins when setting up OAuth details (API > Details > on right, OAuth Details).
How do I add an External OAuth Provider domain with a FAPI security profile?
The Business Admin can configure the FAPI security profile when setting up an External OAuth Provider domain. For more information, see FAPI Support in the External OAuth Provider Domain.
What are the settings on the External OAuth Provider Configure page and what options should I choose?
When you're setting up an External OAuth Provider domain, the Configure page allows you to identify the external provider.
For information about the values set up on the Configure page (Tab 2), refer to the table below.
| Option... | Meaning... |
|---|---|
| Provider Type | The type of external OAuth Provider. If the OAuth Provider is Akana or PingFederate, choose the applicable option. For any other OAuth Provider, choose Other. |
| Configuration Method |
Choose how you want to configure the domain:
|
You can specify the external well-known configuration URLs by adding them to the allowed host list under the Admin section. For more information, see Prevent forward proxying.
What are the settings on the Provider page and what options should I choose?
When you're setting up an External OAuth Provider domain, the Provider page allows you to review information that was read in from the Well-Known Configuration URL or add manual configuration information for your external provider. You can choose not to offer options that your provider supports, by removing configuration values.
For information about the values set up on the Provider page (Tab 3), refer to the table below.
Notes re OAuth URLs:
- In version 2022.1.0 and later, all OAuth URLs must either be on the list of virtual hosts for the tenant (see How do I configure values for a theme?) or must be on the list of trusted hosts in the platform's site settings, Limit forward proxy feature to allow only these hosts field (see How do I configure site settings?).
- If you provided a Well-Known Configuration URL to configure your domain, the values that the provider supports are read from the provider's configuration file and displayed. If you choose not to support some of those values in your External OAuth Provider domain, you can remove those values by clearing the check boxes. The user interface allows you to check additional values; however, if you choose values that the provider doesn't support, the platform cannot support them. Be sure that your configuration reflects only values that your provider supports.
| Option... | Meaning... |
|---|---|
| Issuer | The Issuer ID of the provider. |
| Authorization Endpoint URL | Your provider’s authorization endpoint URL. This is where the provider authenticates the user and requests the user’s consent to allow access to their resources. |
| Token Endpoint URL | Your provider’s token endpoint URL. The token endpoint authenticates the relying party’s request for access. Once authentication is complete, it returns an access token. |
| JWK Set URL | The URI for the JSON web key set where the public key can be read and used for ID token signature validation, if your provider supports sending an ID token signed with a private key. |
| UserInfo Endpoint URL | Your provider's UserInfo Endpoint URL. If you chose to have claims returned from the UserInfo endpoint, the client sends the access token to this endpoint, with information about the claims for which the user granted access permission, and the UserInfo Endpoint returns the user information in the form of a JSON object. |
| Client Registration Endpoint | Optional: The provider's Client Registration endpoint. This allows auto-registration of client apps when they connect to APIs that use this domain. |
| Supported Response Types |
Indicates the OpenID Connect response types that the external OAuth provider is configured to support. If you provided a well-known configuration URL to configure your domain, the supported values are read from the provider's configuration file. Full set of possible options:
|
| Supported Response Modes |
Indicates the OpenID Connect response modes that the external OAuth provider is configured to support. Full set of possible options:
|
| Supported Grant Types |
Indicates the OAuth 2.0 grant types the external OAuth Provider supports. Full set of possible options:
|
| Supported Token Endpoint Authentication Methods |
Authentication methods supported by the token endpoint. Full set of possible options:
Note: If the platform is using PingFederate 9.0x, the app certificate is available and Private Key JWT is enabled here for the domain and also checked in the App OAuth Profile, the platform uses the app's Client Registration JWKS URL in place of the app's certificate/shared secret when synchronizing the app with PingFederate. This also depends on the settings on the Extensions page. For more information, see What are the settings on the External OAuth Provider Extensions page for PingFederate, and what options should I choose? |
| Token Endpoint Auth Signing Algorithm |
Algorithms supported by the token endpoint for signing the token. Full set of possible options:
|
| ID Token Signing Algorithm |
The encryption algorithm that the provider will use to encrypt the ID token signature. Full set of possible options:
|
| ID Token Encryption Key Management Algorithm |
Algorithms supported by this provider for encryption of the ID token key. Full set of possible options:
|
| ID Token Content Encryption Algorithm |
Algorithms supported by this provider for encryption of the ID token content. Full set of possible options:
|
| Scopes Supported |
In the right column, scopes associated with the OAuth Provider are displayed if information was read in. If the OAuth Provider supports additional scopes that are not in the well-known configuration file, you can add those here. You can also use the asterisk wildcard in scopes. Only include one asterisk. As with all fields, do not add values that are not supported by the provider. |
What are the settings on the External OAuth Provider Access Token Validation page and what options should I choose?
When you're setting up an External OAuth Provider domain, the Access Token Validation page allows you to enter information applicable to the OAuth Provider's support of access tokens. The platform can support access tokens issued by PingFederate, the platform itself, or any other OAuth Provider.
For information about the values set up on the Access Token Validation page (Tab 4), refer to the table below. For information about the additional fields available when the OAuth Provider is PingFederate, see What are the settings on the External OAuth Provider Access Token Validation page for PingFederate?
| Option... | Meaning... |
|---|---|
|
JWT Bearer Access Token Referenced Bearer Access Token (PingFederate only) |
Check the applicable check box to access fields for setting up values to support either or both of these token types:
|
Settings for JWT Bearer Access Token
| Option... | Meaning... |
|---|---|
| Issuer | Specify the issuer name that will be in the iss claim of the token. The Resource Server will validate the issuer name against the value provided in this field. |
| Audience |
The value that should be included in the aud (audience) claim in the token. This identifies the entity that will be consuming the token. Enter the value exactly as it is set up in the configuration of your external OAuth Provider. The Resource Server will validate the audience name against the value provided in this field. For multiple values, use a space or comma delimiter. |
| Client ID Claim Name | Claim name the external OAuth Provider uses for the Client ID in the access token. The Resource Server will use the value from this claim to set up the app identity for the request. |
| Scope Claim Name | Claim name the external OAuth Provider uses for a scope in the access token. This claim contains space-delimited scopes that are in the grant scope. The Resource Server will use the value of this claim to check if the request operation can be authorized with the scope of the token. |
| Grant ID Claim Name | Claim name the external OAuth Provider uses for the Grant ID. Each grant represents the resource owners' authorization to the application. The closest standard claim for this is the jti claim. |
| Resource Owner UID Claim Name | Claim name the external OAuth Provider uses for the Resource Owner ID in the access token. |
| Allowed Clock Skew (In Seconds) | The grace period an access token is allowed before effective timestamp and after expired timestamp, expressed in seconds; for example, 120 seconds. This is to accommodate the clock setting difference between the issuing machine and validating machine. At runtime, if clock skew is exceeded, validation fails. |
| Signing Keys |
Choose one of the following:
|
|
Supports Encryption |
Choose one of the following:
|
In PingFederate, the custom claims must not be mapped to Grant Specific claims such as ClientID Claim Name, Scope Claim Name, Grant ID Claim Name, or Resource Owner UID Claim Name. If the custom claims are mapped to Grant Specific claims, they will be skipped from the ResourceOwnerInfo header.
Note: For additional fields available if the provider is PingFederate, see What are the settings on the External OAuth Provider Access Token Validation page for PingFederate?
What are the settings on the External OAuth Provider Access Token Validation page for PingFederate?
When you're setting up an External OAuth Provider domain, the Access Token Validation page allows you to enter information applicable to the OAuth Provider's support of access tokens. The platform can support access tokens issued by PingFederate, the platform itself, or any other OAuth Provider.
When the OAuth Provider is PingFederate, specific fields are available in the right column of the page, that are not available for other providers, as shown below.
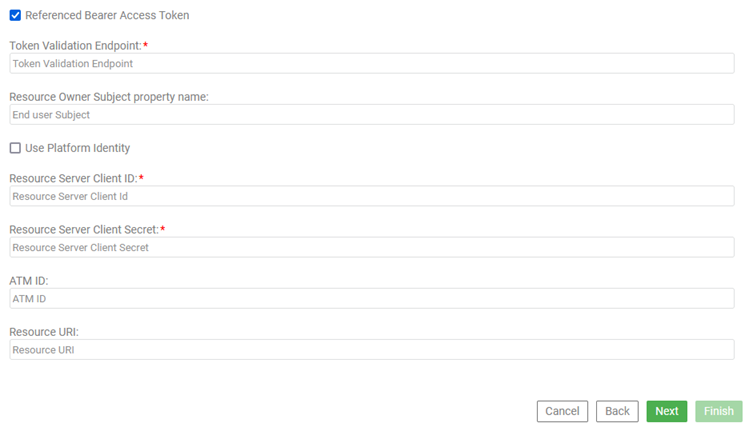
For information about the values specific to PingFederate on the Access Token Validation page (Tab 4), refer to the table below.
Settings for Referenced Bearer Access Token (PingFederate only)
When you choose to verify a Bearer access token with the Authorization Server, this adds a processing step. However, you might prefer to verify the token with the Authorization Server to ensure that any grant revocations are considered when validating the access token.
| Option... | Meaning... |
|---|---|
| Token Validation Endpoint | The endpoint for Bearer access token validation. |
| Resource Owner Subject property name | Property name to be used to identify the resource owner in the Bearer access token validation response. |
| Use Platform Identity | Indicates that the resource server identity information is associated with a platform identity in Policy Manager. Enter the identity name exactly as it is set up in Policy Manager. Make sure identity name and password credentials match with the configured identity for this resource server. Also, be sure to associate an appropriate role in the OAuth Provider to validate bearer access tokens. |
| Platform Client Identity | If you choose to use a platform identity, enter the identity name exactly as it is set up in Policy Manager. Make sure identity name and password credentials match with the configured identity for this resource server. Also, be sure to associate an appropriate role in the OAuth Provider to validate bearer access tokens. |
|
Resource Server Client ID/ Resource Server Client Secret |
If you choose not to use a platform identity, enter the Client ID and password credentials for the account with the external OAuth Provider. |
|
ATM ID Resource URI |
Additional fields needed for PingFederate's support of multiple access token management (ATM) instances. The client can specify an ATM instance by providing either of the following in requests to the PingFederate OAuth Authorization Server:
For more information on these two fields, see https://documentation.pingidentity.com/pingfederate/pf92/index.shtml#adminGuide/tokenEndpoint.html (OAuth access token management parameters section). |
Note: In version 2022.1.0 and later, all OAuth URLs must either be on the list of virtual hosts for the tenant (see How do I configure values for a theme?) or must be on the list of trusted hosts in the platform's site settings, Limit forward proxy feature to allow only these hosts field (see How do I configure site settings?).
What are the settings on the External OAuth Provider Extensions page for PingFederate, and what options should I choose?
If your external OAuth Provider is PingFederate, you'll see some additional choices available on the Extensions page of the wizard. These settings represent additional functionality supported by PingFederate. The page will look something along the lines of the below.
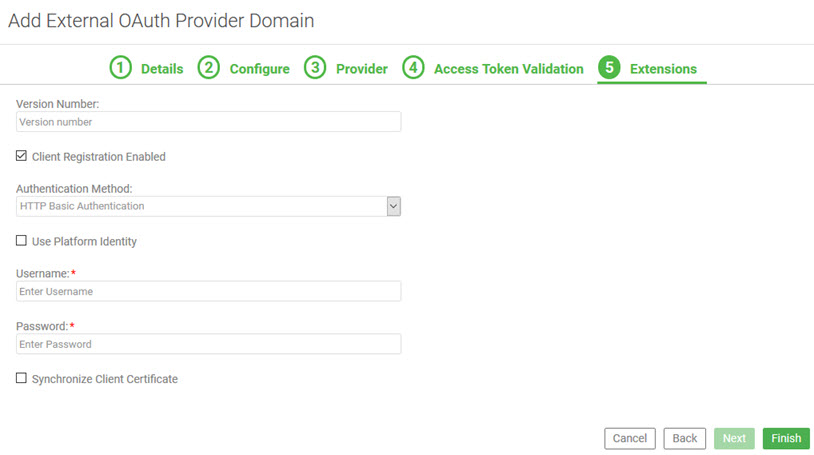
For information about the values you can set up for your PingFederate OAuth Provider on the Extensions page (Tab 5), refer to the table below.
| Option... | Meaning... |
|---|---|
| Version Number |
Specify the PingFederate version number you're using, in the format major.minor; for example, 8.0, 8.3, or 9.0. For information about the PingFederate versions the platform supports, see What versions of PingFederate does the platform support? |
| Client Registration Enabled | Check this box if your implementation is using the client registration endpoint. This allows auto-configuration of apps that have active contracts with APIs that reference the External OAuth Provider domain. Manual configuration of the apps in PingFederate is not necessary. |
| Authentication Method | Choose the authentication method out of the options available. |
| Use Platform Identity | Indicates that the credentials are associated with a platform identity in Policy Manager. For more information, see Should I set up a platform identity, or provide the credentials in the domain configuration? |
| Platform User Identity | Enter the identity name exactly as it is set up in Policy Manager. |
| Username/Password | The username and password credentials that identify the platform with PingFederate |
| Synchronize Client Certificate |
Determines whether apps contracted with APIs that use this OAuth domain can authenticate with PingFederate using a certificate uploaded to the app's OAuth Profile page. Options are as follows:
Note: If you're using PingFederate 9.x and Client Registration and the Synchronize Client Certificate settings are both enabled, the app certificate is available and Private Key JWT is checked in the app's OAuth Profile page, the platform uses the app's Client Registration JWKS URL in place of the app's certificate/shared secret when synchronizing the app with PingFederate. This also requires that Private Key JWT is enabled in the External OAuth Provider Domain setup, Provider tab, in the Supported Token Endpoint Authentication Methods field. |
How do I modify an External OAuth Provider domain?
If there are changes to your External OAuth Provider domain configuration, you'll need to update the domain settings in the platform.
Note: The procedure below only updates the platform settings; it doesn't change any external configuration with the external OAuth Provider. To change to the external OAuth Provider configuration, you must first make the changes with the provider itself, and then update the platform settings to match the provider configuration, using the procedure below.
To modify an External OAuth Provider domain in the Community Manager developer portal
- Log in as a Business Admin and go to the Admin section.
- Click Domains. The Domains Summary page displays.
- Find the domain on the list and click Modify. The Edit wizard for the specific domain type displays.
- Change values as needed.
- Click Save. The changes might take a few minutes to take effect.
How do I delete an External OAuth Provider domain?
To delete an External OAuth Provider domain
- Log in as a Business Admin and go to the Admin section.
- Click Domains. The Domains Summary page displays.
- In the right-hand column of the domain line item, click Delete. At the confirmation message, click OK.
Note: Rather than deleting a domain, you might choose to disable the domain for login. For instructions, see How do I disable a platform login?
How do I monitor the PingFederate Client Registration Status?
The alerts and email notifications are generated for PingFederate when synchronizing client registration status for scheduled job success and error results. This may occur for the following reasons.
- Any exception in connecting to PingFederate due to an expired certificate or invalid credentials.
- Runtime errors such as timeout or connectivity issues.
- Success or failure in synching a particular app.
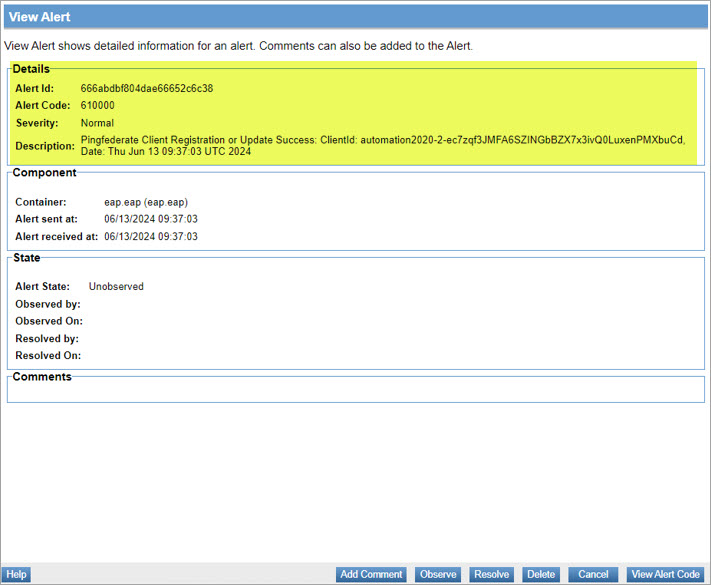
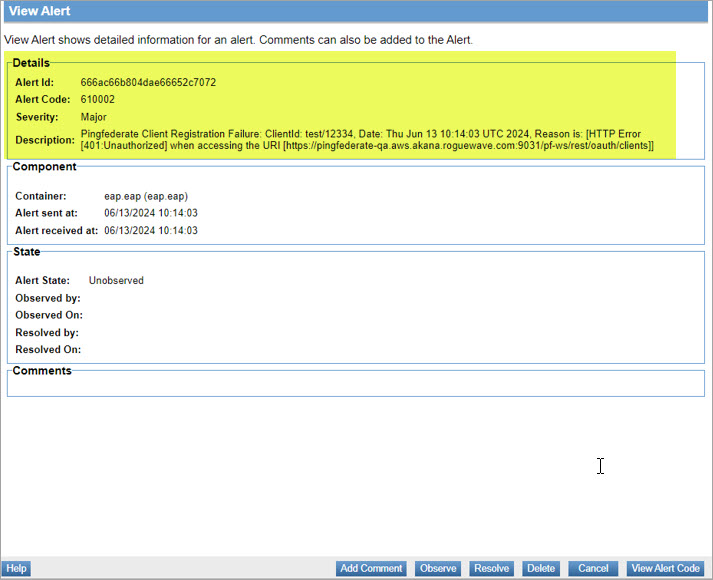
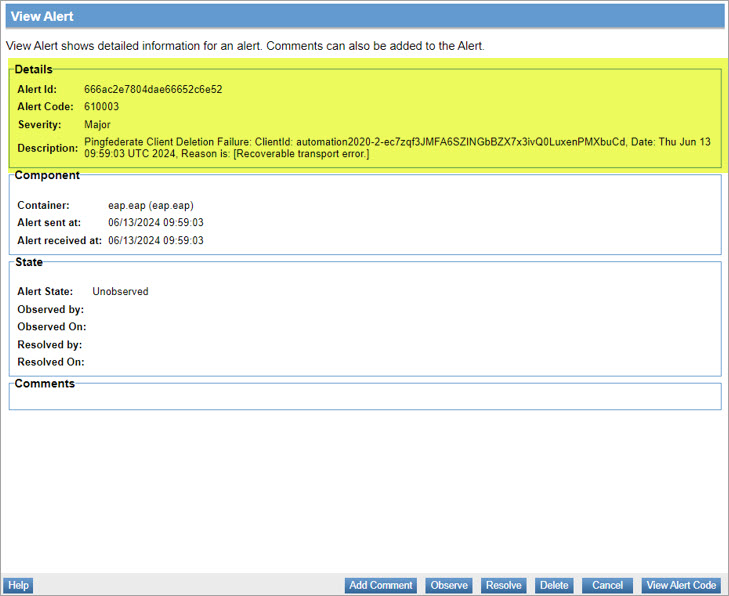
The associated alert code information including Alert ID, Alert Code, Severity, and Description for an alert is generated in the Policy Manager console.
Code 610000 - Alert for PingFederate client registration success
Code 610001 - Alert for PingFederate client deletion success

Code 610002 - Alert for PingFederate client registration failure
Code 610003 - Alert for PingFederate client deletion failure
How do I configure encryption key rotation for an External OAuth Provider domain?
The External OAuth Provider domain can be configured with multiple platform identities using rotating encryption keys. The key rotation is when a signing key is retired and replaced by generating a new key. The main reason for rotating encryption keys is to decrease the amount of data encrypted with a specific key, thereby reducing the potential impact of a security breach.
The Akana External OAuth Provider domain allows you to configure multiple platform identities as a comma-separated list of identities (encryption keys) on the External OAuth Provider Access Token Validation page by selecting the checkbox "Supports Encryption / Reference encryption keys from an existing platform identity". This feature enables JWT encryption key rotation on External OAuth Provider. During the key rotation period, the current identity (close to expiration) and the new identity (after expiration) will be used to decrypt the token.
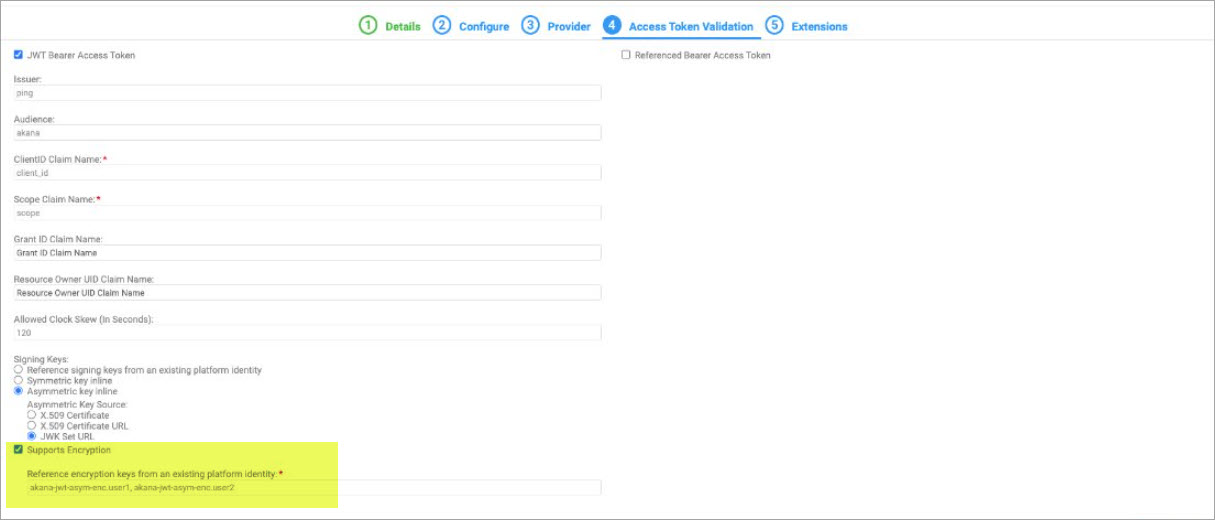
To support encryption key rotation, the JWE token must include a "kid" header that matches the name of an identity configured in the Akana Platform. See Setting up the JWE Kid header for PingFederate.
Setting up the JWE Kid header for PingFederate
If your external OAuth Provider is PingFederate and you want to generate the access token using key rotation, then you must configure PingFederate to include an identifier that identifies the key used to encrypt the token. To configure multiple platform identities as encryption keys, include the JWE Key ID (kid) header and JWE X.509 Thumbprint header parameter in the encryption header of the token to identify the appropriate key during decryption.
Use the Access Token Management to specify how the PingFederate manages access tokens. Go to Applications > OAuth > Access Token Management.
In the Access Token Management, select the checkbox to include JWE Key ID header and JWE X.509 Thumbprint header parameter.
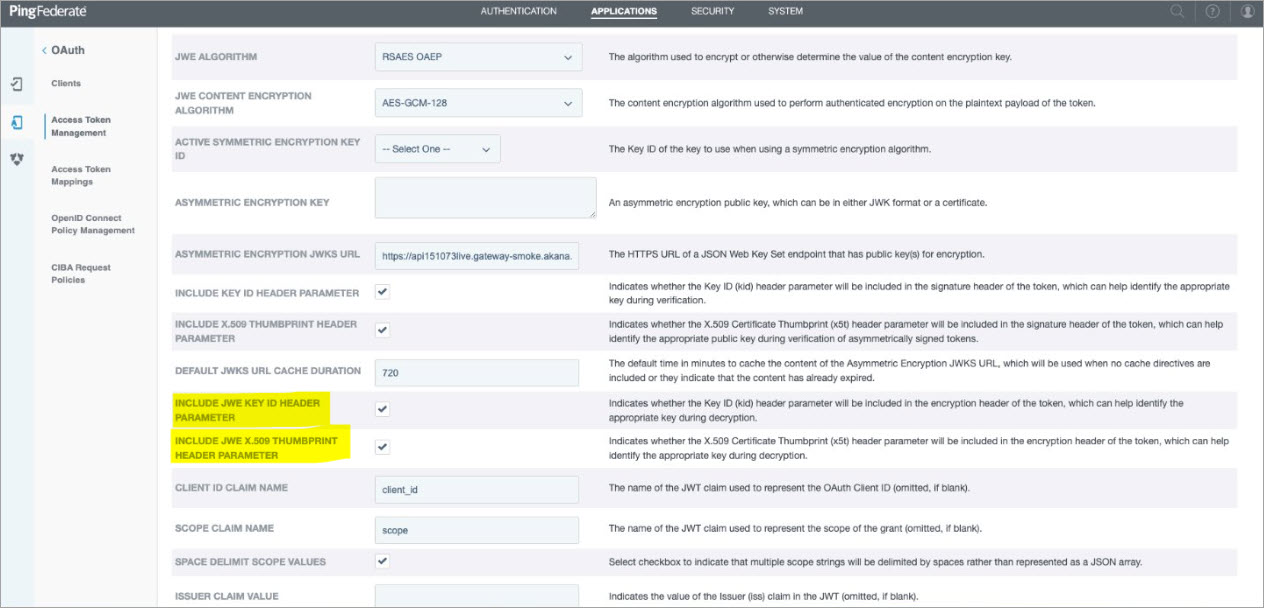
After you have selected the header parameters in PingFederate, the JWE Key ID is used to rotate the encryption keys, allowing the token to be securely encrypted and decrypted.
After making changes to PingFederate, you must update the platform settings by selecting the checkbox "Supports Encryption / Reference encryption keys from an existing platform identity" from the Access Token Validation page.